Today’s post will cover the burning issue confronting any Cloud Solution and that is none other than security. With the growing scope and application of cloud solutions, more and more participants of the organization and organizations of every scale are availing the cloud and why not as it brings a lot of benefits to the organization.

Previously, the primary and perhaps only users of cloud were the management and employees of an organization. This sphere has now increased to include external stakeholders like suppliers, vendors and even end customers.
So, this change in the spectrum of cloud users poses an even bigger challenge to Cloud Security. It is relatively quite easy to regulate and manage the cloud access of employees as they are bound by many organizational policies and checks.
This however does not apply to external stakeholders of an organization, who are not bound by any such limitation. So, they are more likely to commit the very security lapses that pose concerns for managers of any cloud’s security.
Concept of Zero Trust Security
This is where the ingenious approach of Zero Trust Security comes in. Under this approach, an organization will not pick and choose among the cloud users when it comes to security privileges. In this approach, every cloud user, internal or external is treated equally and a potential threat to security.

In the present day and age of extremely covert phishing and malware practices, the basic security barriers comprising of passwords are virtually irrelevant. In many instances, the owner of a password realizes the misuse of the same, much after some substantial damage has been inflicted.
Why Companies Need To Develop Zero Trust Model?
To practically implement the Zero Trust model, the first step an organization has to take is adopt a uniform mechanism for authenticating a cloud user. This applies equally to both internal and external users of the cloud solution.
Secondly, this authentication will be placed at the very access point of the cloud, so that no unauthorized access whatsoever is granted to an uninvited guest on the cloud. Once the access has been granted post authentication, then the cloud’s mechanism would grant further access to each and every tier of the organization purely on a need basis.
Some Physical Aspects of Zero Trust Security Model
Now that we have covered the basics of Zero Trust Security Model, let’s discuss a few practical aspects of this approach. The foremost step in the process is user authentication. The best and safest barrier to any unintended access to the cloud is at the entry level.
Passwords used to be a very effective tool back in the days but today’s multidimensional platforms have rendered them defenseless. The solution to access related security is thus multi-factor authentication.
What multi-factor authentication implies is that the cloud’s access system will not merely rely on a single parameter such as a correct password to grant access. At least two different means of identifying the user will be used before granting access to the cloud.
The traditional password will grant initial access to the system and require at least one more “dynamic” parameter for full access. These dynamic or variable parameters may be a person’s fingerprint or a portable device that generates a random code on a periodic basis.
In the presence of this dynamic layer of authentication, even if a person lays his hands on a user’s password, access to the cloud will still not be granted as the additional layer of security will need to be passed. This scenario is next to impossible and thus enhances the cloud’s security manifolds.
Another key advantage of the Zero Trust approach is that once a dynamic security layer has been agreed upon, it can and should be implemented across the organization. Every user who accesses the cloud will be subjected to the same level of authentication before access is granted.
How dinCloud is Implementing Zero Trust Security Strategy?
dinCloud is at the forefront of implementing the Zero Trust Security Strategy. Although this added layer entails incremental costs, but the long-term security benefits of this approach far outweigh the costs. This by no means implies that the security measures already in place at dinCloud are by any means inferior.
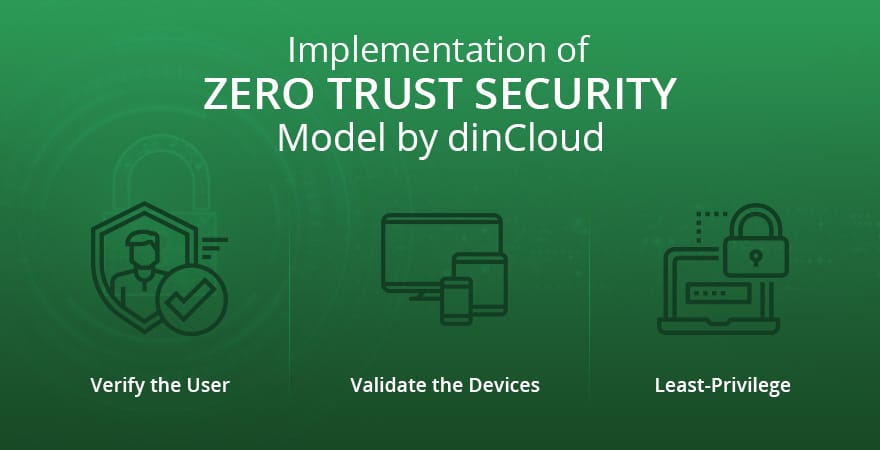
The obvious limitation is that most security measures end at the level of access. Once an unauthorized user gains access to the cloud infrastructure, the potential risks can be catastrophic. In extreme cases where the user who is impersonated had high level access to the cloud infrastructure, the organization may suffer irreparable damage.
Conclusion
Although the concept of Zero Trust Security Strategy is relatively new, organizations must adopt a proactive approach and embrace this measure as more of a necessity, rather than a luxury. It goes without saying that you can always trust dinCloud and its professionals to chalk out the best possible multi-level authentication solution for your needs.


