Cloud based or on-premise, the digital footprint of enterprises is constantly expanding. Enterprises are being driven into rapid digitalization as a pressing business need, and most have little choice but to follow suit.
However, this enlarged digital footprint of organizations, which extends way beyond their physical boundaries, also brings along its fair share of cyber security and regulatory compliance challenges.
An expanded digital footprint is just one part of the problem, as cyber threats such as ransomware, malware and deeply embedded vulnerabilities are expanding the risk canvas for enterprises to unprecedented levels.
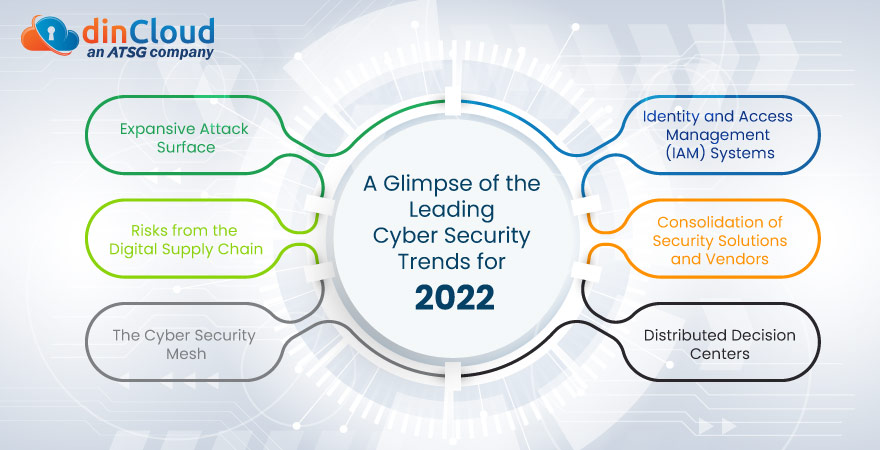
In this post, we will take a glimpse of the major Cyber Security trends for the year 2022. We will also touch upon the areas where Chief Information Officers (CIOs) and Chief Information Security Officers (CISOs) should focus for a robust cyber security posture.
Related: The Top Cyber Security Challenges for Year 2022
Expansive Attack Surface
In the present circumstances, factors such as extended remote work and hybrid work models have resulted in a constantly expanding attack surface. CISOs will have to cope with this reality. A recent survey reveals that nearly 60% of knowledge workers are now remote.
Out of these knowledge based workers, who have both the skillset and temperament to work remotely full time, an estimated 18% of these knowledge workers have no plans of returning to the physical workplace. This makes remote work a perpetual aspect of security.
Identity and Access Management (IAM) Systems
A recent study by Gartner has revealed that Identity and Access Management (IAM) systems will continue to be a prized target for cyber attackers. Recent high profile data and security breaches have clearly pointed out towards this problem.
Vulnerabilities, coupled with the prevalent issue of credential theft, have enabled cyber miscreants to gain access to power users with high profile access and privileged rights. Using them as the entry vector, hackers have been able to wreak havoc.
Enterprises can address Identity and Access Management threats by giving even the power users a role based access to high level resources and data. That way, even if there is a credential theft or data breach, the extent of damage will be much contained.
Related: How is Cloud Computing Bolstering Industrial Cyber Security and Productivity?
Risks from the Digital Supply Chain
In a bid to streamline their processes and boost employee productivity, enterprises often resort to third party software solutions. While there is no harm in doing so, the “digital and security hygiene” of these solutions will need to be thoroughly evaluated by enterprises.
One way of mitigating digital supply chain related risks is to closely engage with the software suppliers and vendors. This will give deploying enterprises better visibility into whether such entities adhere to the best practices for software development, and so forth.
Related: dinCloud adds Sophos Intercept X to its Cyber Security Arsenal
Consolidation of Security Solutions and Vendors
While consolidating all your security mechanisms and vendors may seem like an approach that is akin to “putting all your eggs in one basket”, experts believe this will ultimately evolve into something that clients will actually need over the long term.
Although Gartner believes that doing so will result in a reduced bargaining power, so far enterprises are concerned that consume such consolidated solutions, this approach will prove beneficial for deploying enterprises.
By consolidating the disparate security mechanisms and vendors at a single place, enterprises will be able to introduce uniformity and ease of management, when it comes to managing their cyber security and data privacy risk postures.
Related: The Cyber Security Outlook by Gartner for 2022 and Beyond
The Cyber Security Mesh
As the name suggests to quite an extent, this trend in enterprise cyber security involves extending the cyber security bubble, or envelope across the full length and breadth of an organization’s assets and infrastructure.
Ideally, the cyber security mesh will fully encompass the on-premise, hybrid and cloud based infrastructures, deployments or environments of an enterprise. This approach also encapsulates in-office, remote and hybrid work models.
By adopting an effective cyber security mesh approach to their infrastructure, Gartner believes enterprises will be able to reduce the financial impact or fallout of cyber security related incidents by as much as a whopping 90%.
Distributed Decision Centers
According to this emerging trend in enterprise cyber security, some elements of cyber risk will need to be centralized, while the others will need to be de-centralized, depending upon the criteria such as geographical location, regulatory needs or localized laws.
Essentially, the CISO will continue to play the role of an organization wide watchdog, but the individual, granular level aspects of enterprise cyber security and compliance posture will be managed, as well as tweaked by localized CIOs and CISOs.
Conclusion
The constantly expanding digital footprint of enterprises is bringing a lot of flexibility and agility to enterprise operations. However, this approach also brings along its fair share of challenges and roadblocks, which we have tried to cover in this post.
At the end of the day, it all boils down to having a proactive approach towards managing the cyber security risk posture of an enterprise. As enterprises cannot afford to be left out anymore, it is more about managing your cyber security risks, rather than total isolation.
Contact dinCloud, an ATSG company, for highly secure, compliant and robust Cloud Hosted Virtual Desktop solutions that will considerably bolster your overall cyber security posture.


